Breadcrumb
An approach for extracting and disambiguating arabic persons' names using clustered dictionaries and scored patterns
Building a system to extract Arabic named entities is a complex task due to the ambiguity and structure of Arabic text. Previous approaches that have tackled the problem of Arabic named entity recognition relied heavily on Arabic parsers and taggers combined with a huge set of gazetteers and sometimes large training sets to solve the ambiguity problem. But while these approaches are applicable to modern standard Arabic (MSA) text, they cannot handle colloquial Arabic. With the rapid increase in online social media usage by Arabic speakers, it is important to build an Arabic named entity
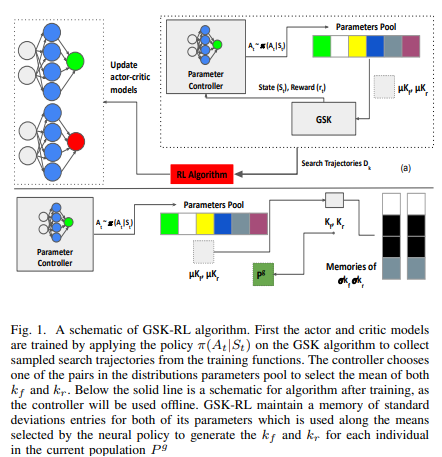
GSK-RL: Adaptive Gaining-sharing Knowledge algorithm using Reinforcement Learning
Meta-heuristics and nature inspired algorithms have been prominent solvers for highly complex, nonlinear and hard optimization problems. The Gaining-Sharing Knowledge algorithm (GSK) is a recently proposed nature-inspired algorithm, inspired by human and their tendency towards growth and gaining and sharing knowledge with others. The GSK algorithm have been applied to different optimization problems and proved robustness compared to other nature-inspired algorithms. The GSK algorithm has two main control parameters kfand kr which controls how much individuals gain and share knowledge with
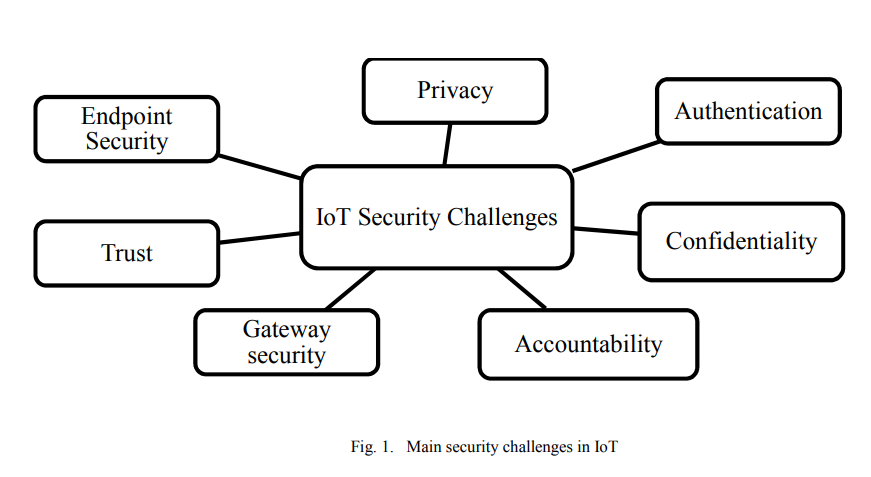
Internet of Things security framework
For the past decade, Internet of Things (IoT) had an important role in our lives. It connects a large number of embedded devices. These devices fulfill very difficult and complicated tasks, which facilitate our work. Till now the security of IoT faces many challenges such as privacy, authentication, confidentiality, trust, middleware security, mobile security and policy enforcement. In order to provide a secure environment for IoT, this paper proposes a framework for IoT devices. © 2017 IEEE.
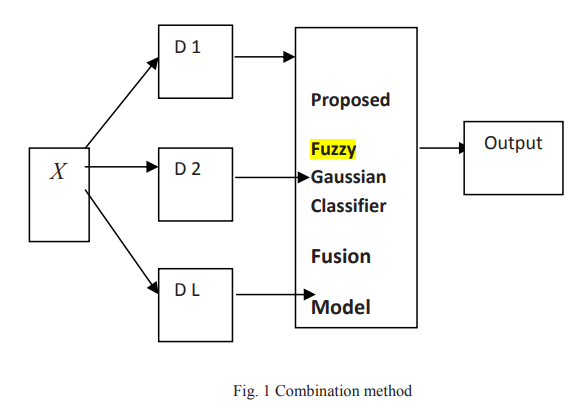
Fuzzy gaussian classifier for combining multiple learners
In the field of pattern recognition multiple classifier systems based on the combination of outputs from different classifiers have been proposed as a method of high performance classification systems. The objective of this work is to develop a fuzzy Gaussian classifier for combining multiple learners, we use a fuzzy Gaussian model to combine the outputs obtained from K-nearest neighbor classifier (KNN), Fuzzy K-nearest neighbor classifier and Multi-layer Perceptron (MLP) and then compare the results with Fuzzy Integral, Decision Templates, Weighted Majority, Majority Naïve Bayes, Maximum
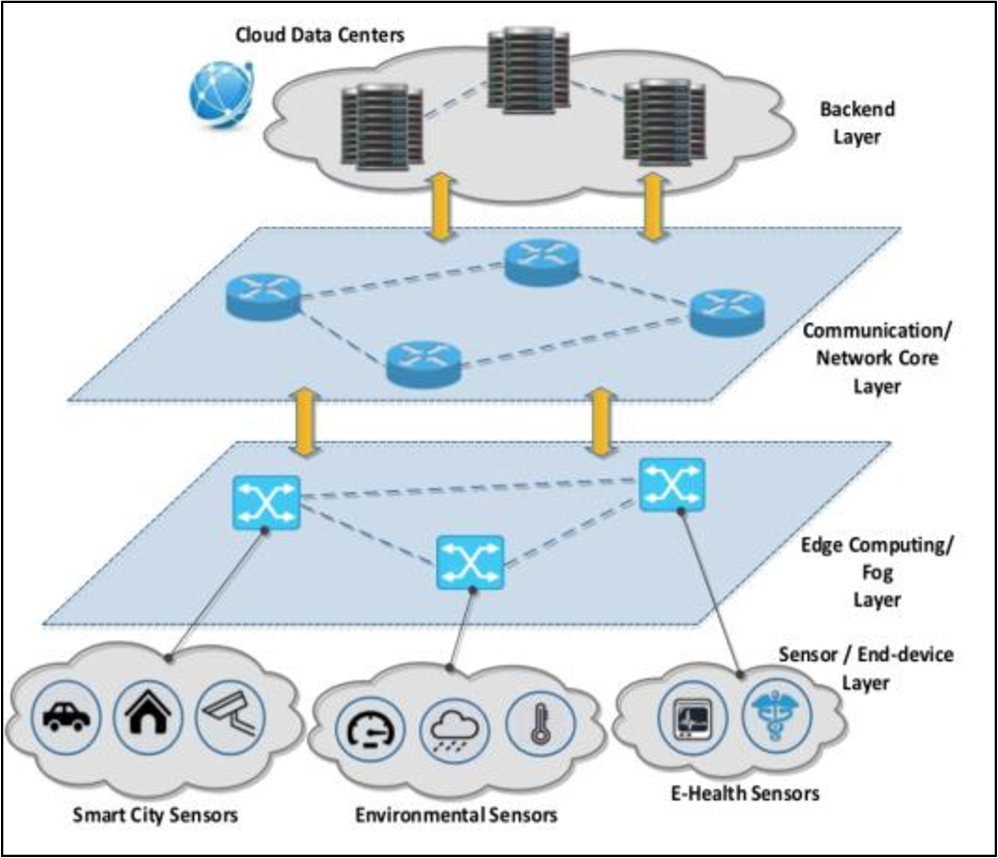
IoT Modes of Operations with Different Security Key Management Techniques: A Survey
The internet of things (IoT) has provided a promising opportunity to build powerful systems and applications. Security is the main concern in IoT applications due to the privacy of exchanged data using limited resources of IoT devices (sensors/actuators). In this paper, we present a classification of IoT modes of operation based on the distribution of IoT devices, connectivity to the internet, and the typical field of application. It has been found that the majority of IoT services can be classified into one of four IoT modes: Gateway, device to device, collaborative, and centralized. The
Pagination
- Previous page ‹‹
- Page 2
