Breadcrumb
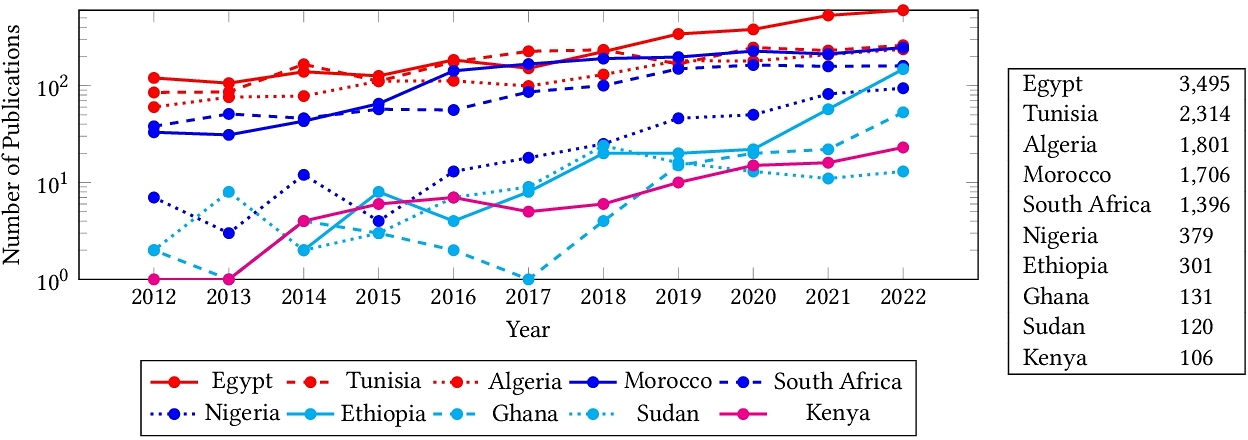
The State of Computer Vision Research in Africa
Despite significant efforts to democratize artificial intelligence (AI), computer vision which is a sub-field of AI, still lags in Africa. A significant factor to this, is the limited access to computing resources, datasets, and collaborations. As a result, Africa's contribution to top-tier publications in this field has only been 0.06% over the past decade. Towards improving the computer vision field and making it more accessible and inclusive, this study analyzes 63,000 Scopus-indexed computer vision publications from Africa. We utilize large language models to automatically parse their
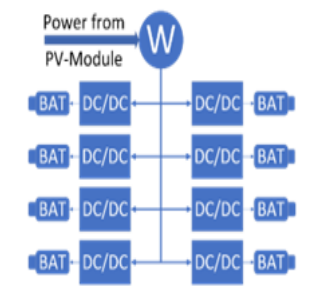
Developing Role Model of PV Powered Battery Swapping Stations for e-scooters in Urban Regions
Electric vehicles (EVs) can only provide lower carbon emissions than conventional, internal combustion-powered vehicles if they are charged using green energy. They also have the drawback of long charging times to 'refuel' them. To combat these two problems, a solar-powered battery charging and swapping station was developed using centered-human design and systems engineering. The design focuses on electric two-wheeled vehicles (e-scooters) due to the easier handling of their light and low-capacity batteries compared to electric cars. These stations are easy to maintain and manage and can be
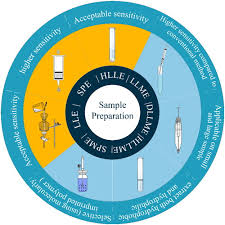
Analytical Methods for the Determination of Quercetin and Quercetin Glycosides in Pharmaceuticals and Biological Samples
Flavonoids are plant-derived compounds that have several health benefits, including antioxidative, anti-inflammatory, anti-mutagenic, and anti-carcinogenic effects. Quercetin is a flavonoid that is widely present in various fruits, vegetables, and drinks. Accurate determination of quercetin in different samples is of great importance for its potential health benefits. This review, is an overview of sample preparation and determination methods for quercetin in diverse matrices. Previous research on sample preparation and determination methods for quercetin are summarized, highlighting the

Computational Intelligence for Medical Internet of Things (MIoT) Applications
Computational Intelligence for Medical Internet of Things (MIoT) Applications: Machine Intelligence Applications for IoT in Healthcare explores machine intelligence techniques necessary for effective MIoT research and practice, taking a practical approach for practitioners and students entering the field. This book investigates advanced concepts and applications in the MIoT field, guiding readers through emerging developments and future trends. A wide range of international authors guide readers through advanced concepts, including deep learning, neural network, and big data analytic
NGU_CNLP at WANLP 2022 Shared Task: Propaganda Detection in Arabic
This paper presents the system developed by the NGU_CNLP team for addressing the shared task on Propaganda Detection in Arabic at WANLP 2022. The team participated in the shared tasks' two sub-tasks which are: 1) Propaganda technique identification in text and 2) Propaganda technique span identification. In the first sub-task the goal is to detect all employed propaganda techniques in some given piece of text out of a possible 17 different techniques, or to detect that no propaganda technique is being used in that piece of text. As such, this first sub task is a multi-label classification
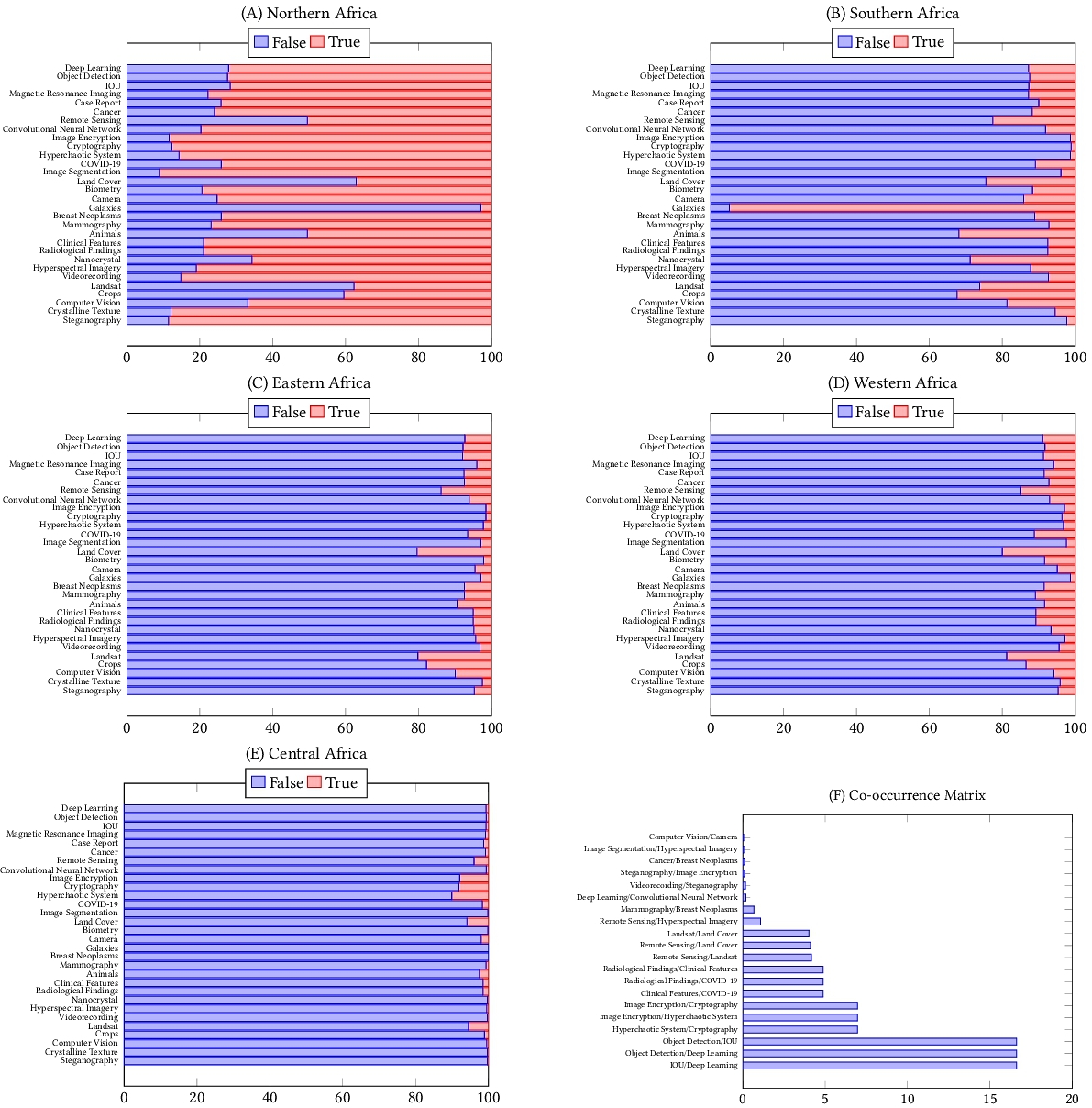
Towards a Better Understanding of the Computer Vision Research Community in Africa
Computer vision is a broad field of study that encompasses different tasks (e.g., object detection, semantic segmentation, 3D reconstruction). Although computer vision is relevant to the African communities in various applications, yet computer vision research is under-explored in the continent and constructs only 0.06% of top-tier publications in the last ten years. In this paper, our goal is to have a better understanding of the computer vision research conducted in Africa and provide pointers on whether there is equity in research or not. We do this through an empirical analysis of the
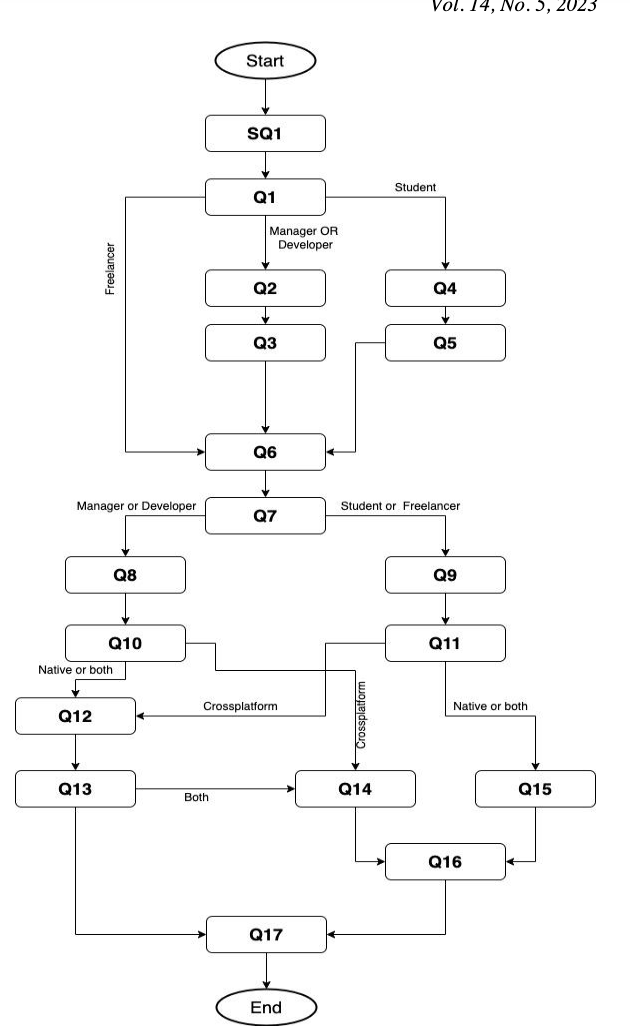
Industrial Practitioner Perspective of Mobile Applications Programming Languages and Systems
The growth of mobile application development industry made it crucial for researchers to study the industry practices of choosing mobile applications programming languages, systems, and tools. With the increased attention of cross-platform mobile applications development from both researchers and industry, this paper aims at answering the question of whether most of the industries are using cross-platform development or native development. The paper collects feedback about industry’s most used mobile development systems. In addition, it provides a map of the different technologies used by
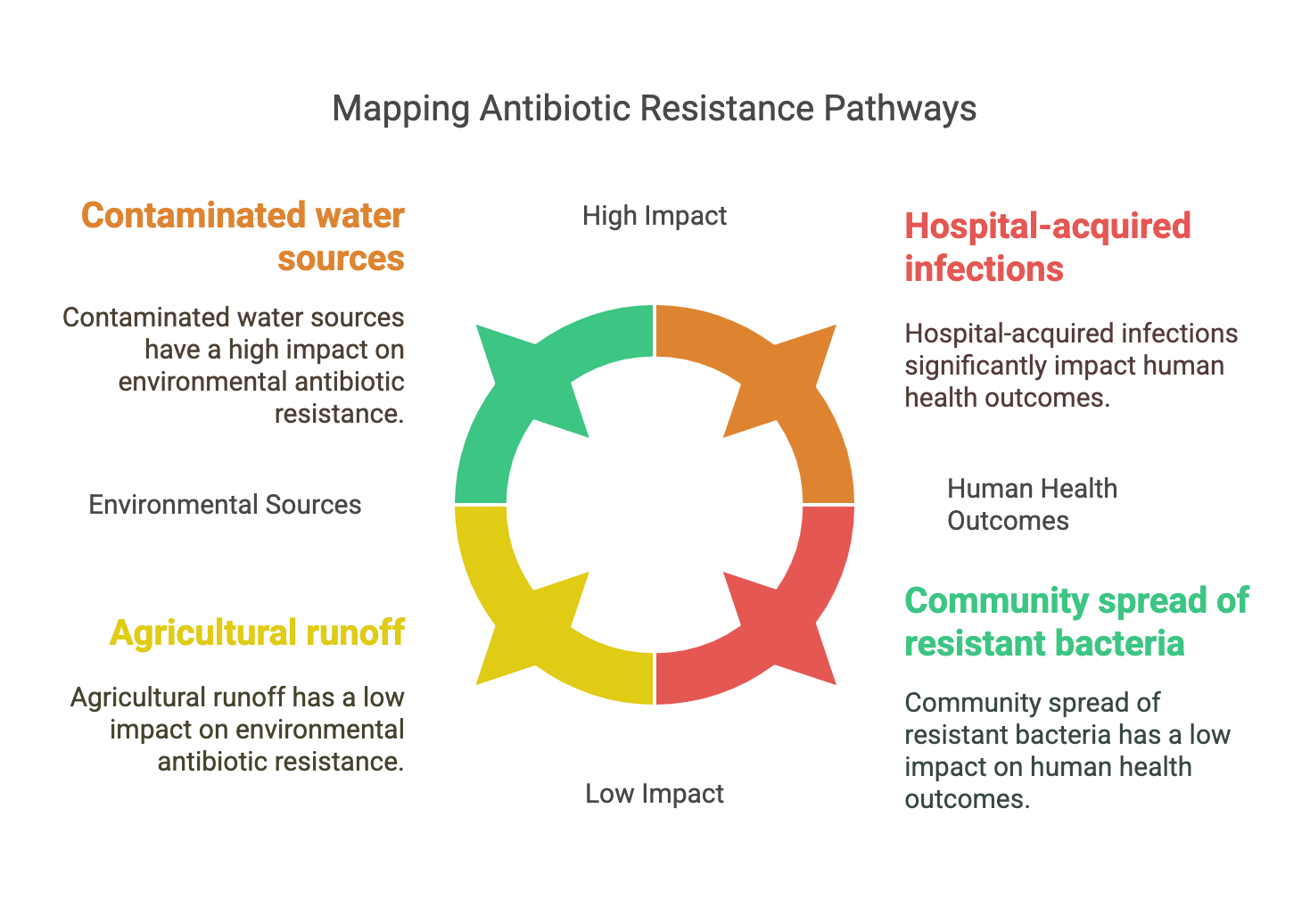
Tracking Antibiotic Resistance from the Environment to Human Health
Antimicrobial resistance (AMR) is one of the threats to our world according to the World Health Organization (WHO). Resistance is an evolutionary dynamic process where host-associated microbes have to adapt to their stressful environments. AMR could be classified according to the mechanism of resistance or the biome where resistance takes place. Antibiotics are one of the stresses that lead to resistance through antibiotic resistance genes (ARGs). The resistome could be defined as the collection of all ARGs in an organism’s genome or metagenome. Currently, there is a growing body of evidence

A distributed real-time recommender system for big data streams
Recommender Systems (RS) play a crucial role in our lives. As users become continuously connected to the internet, they are less tolerant of obsolete recommendations made by an RS. Online RS has to address three requirements: continuous training and recommendation, handling concept drifts, and the ability to scale. Streaming RS proposed in the literature address the first two requirements only. That is because they run the training process on a single machine. To tackle the third challenge, we propose a Splitting and Replication mechanism for distributed streaming RS. Our mechanism is inspired
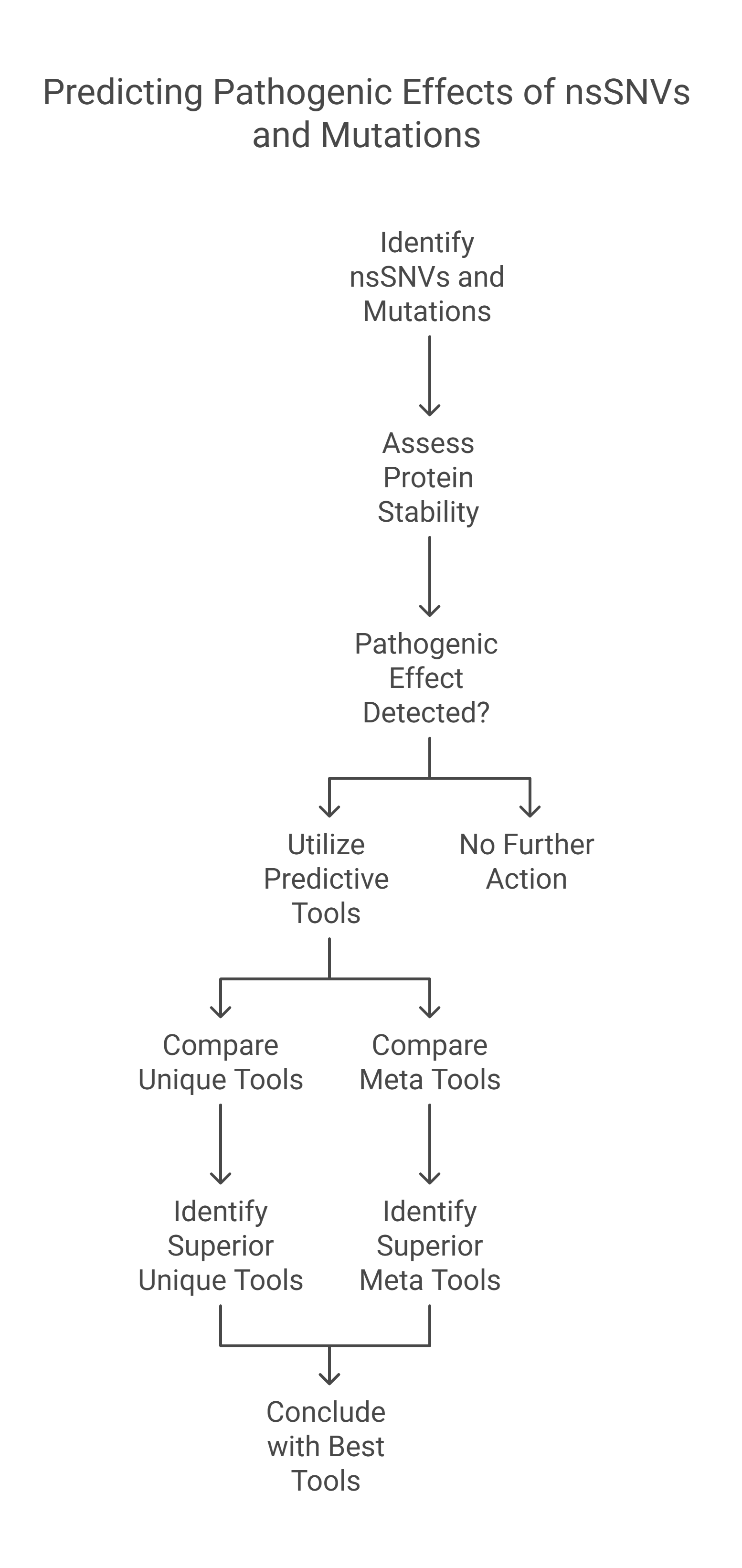
Predicting non-synonymous single nucleotide variants pathogenic effects in human diseases
Non-synonymous Single - Nucleotide Variants (nsSNVs) and mutations can create a diversity of the contrary influence of proteins like varying genotype and phenotype of any protein which affects its stability. The alterations in the protein stability may cause diseases. Detecting of nsSNVs and mutations can be a helpful tool in diagnosing diseases at an early stage. The study of singular and consensus tools for predicting pathogenic effects is very essential. Many studies utilized various predicting servers based on distinct Machine Learning Techniques (MLTs). In this research, we conduct a
Pagination
- Previous page ‹‹
- Page 6
- Next page ››
